- Lab 8.4.1.3 Configure Site To Site Vpn Using Cli
- 8.4 1.3 Lab Site To Site Vpn Using Cli Commands
- 8.4 1.3 Lab Site To Site Vpn Using Cli Chrome
- 8.4 1.3 Lab Site To Site Vpn Using Cli Vpn
Always select the correct lab exercise for the lab being performed. Students or teams should schedule the correct lab exercise from the catalog. NETLAB+ will only show those labs for which the required pod type is available. A lab that works on different pod types may appear more than once if your system is so equipped. Instructors should select the correct lab from the Exercise tab during instructor-led lab reservations. This can be done as many times as needed during the reservation.
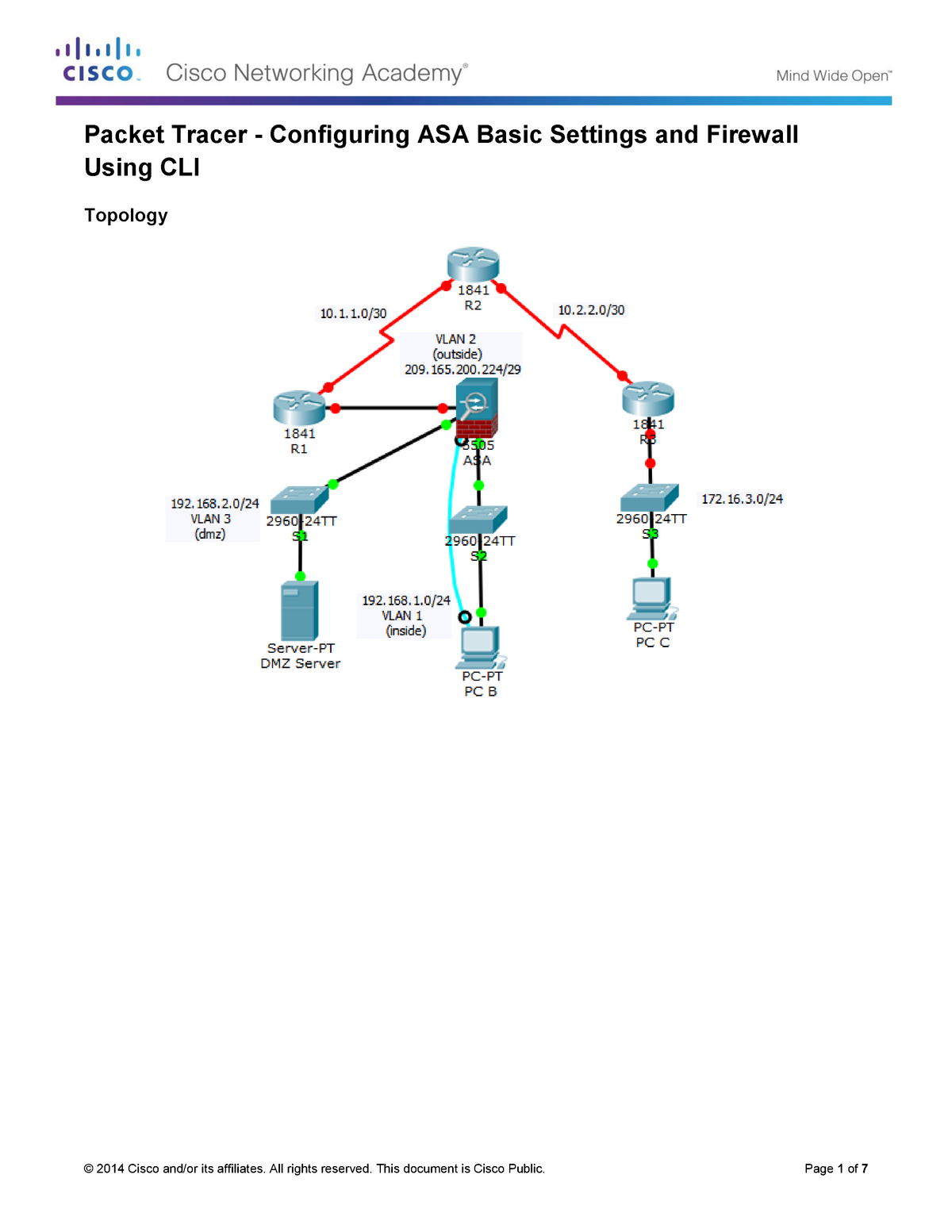
Packet tracer 6.3.1.3: Layer 2 VLAN Security packet tracer 8.4.1.2 Configure and Verify a Site-to-Site IPsec VPN using CLI packet tracer 9.3.1.1 Configuring ASA Basic Settings and Firewall Using CLI.
- Configure and Verify a Site-to-Site IPsec VPN using CLI بالعربي Configure and Verify a Site-to-Site IPsec VPN using.
- Lab 6.3.1.3 Packet Tracer Layer 2 VLAN Security Oct 19 7 6 Cryptographic Systems Oct 21 Exploring Encryption Methods Oct 26 8 7 Implementing Virtual Private Networks Oct 28 Configuring a Site-to-Site VPN Using Cisco IOS and CCP Lab 8.4.1.2 Packet Tracer Configure and Verify a Site-to-Site IPsec VPN using CLI.
Importance of Choosing the Correct Lab Exercise
Several of the labs may differ from the standard pod topologies. This is handled by NETLAB+ Dynamic VLAN Mapping technology. Always select the correct lab exercise for the actual lab. This insures that NETLAB+ will set up VLANs on the control switch such that lab devices and PCs are placed in the correct LAN segment for the exercise being performed. Selecting the correct exercise will also make the completed lab output easier to find in the archive.
Lab 8.4.1.3 Configure Site To Site Vpn Using Cli
NETLAB+ will configure the routers and switches with initial configuration files that include basic IP connectivity. Please verify this configuration by pinging the network interfaces before starting the lab exercise.


A common requirement with Site-to-Site tunnels is access-control through the tunnel. One strategy to accomplish this might be to have a rather complex crypto ACL. But this leads to additional administration overhead as there is actually a pair of IPsec SAs for each active
entry in the crypto ACL. The proper way to limit traffic through a Site-to-Site tunnel with the ASA is to apply a filter via group policy. In this section of the lab, you will prevent Site1 systems from reaching the management subnet.
1. Create an ACL which denies access to 10.10.2.0/24 for use as a filter for the Site1 VPN
Navigate to Configuration > Site-to-Site VPN > Advanced > ACL Manager
The table of ACLs defined on the ASA appears.
Click Add > Add ACL.
Enter the name Site1-VPN-Filter and click OK.
With Site1-VPN-Filter highlighted in the table, click Add > Add ACE.
Define the first Access Control Entry as follows:
• Action: Deny
• Source: Any
• Destination: 10.10.2.0/24
• Service: ip
Leave other options at their default values and click OK.
Select the first line in the Site1-VPN-Filter and select Add > Add ACE.
Define the first Access Control Entry as follows:
• Action: Permit
• Source: Any
• Destination: Any
• Service: ip
Leave other options at their default values and click OK.
Click Apply.
8.4 1.3 Lab Site To Site Vpn Using Cli Commands
2. Modify the group policy for Site1-VPN, and select the new ACL as the filter:
Navigate to Configuration > Site-to-Site VPN > Group Policies
Select the Site1-Policy and click Edit.
Modify the group policy as follows:
• IPv4 Filter: Uncheck Inherit and select Site1-VPN-Filter
Leave the other values at their defaults and click OK.
Click Apply.
The policy is defined, but it won’t take effect until the next time the Site1 VPN tunnel is negotiated.
8.4 1.3 Lab Site To Site Vpn Using Cli Chrome
3. “Bounce” the Site1 tunnel:
Navigate to Monitoring > VPN > VPN Statistics > Sessions
Set the filter to IPsec Site-to-Site.
If the tunnel to 200.200.20.2 is still active, click Logout.
8.4 1.3 Lab Site To Site Vpn Using Cli Vpn
Posted in ASA Site-to-Site VPN, Network Security
