- Asa Route Map California
- Asa Route Map Directions
- Cisco Asa Route-map Nat
- Asa Route Map New York
- Asa Route Map Location
- Asa Route Map Definition
Cisco ASA using multiple Nat/Global commands to nat source IPs to specific public addresses (3 subnets). And then a Cisco router doing PBR to send outbound t. Enter your addresses and get the shortest driving directions. Traffic & Weather included. The PBR on the Cisco ASA works similarly to the one on Cisco routers – we use route-maps to configure policies and these route-maps are then applied to an interface. With PBR, we can match based on several criteria such as source and/or destination address/port, protocol and so on and then perform actions such as setting a specific next-hop.
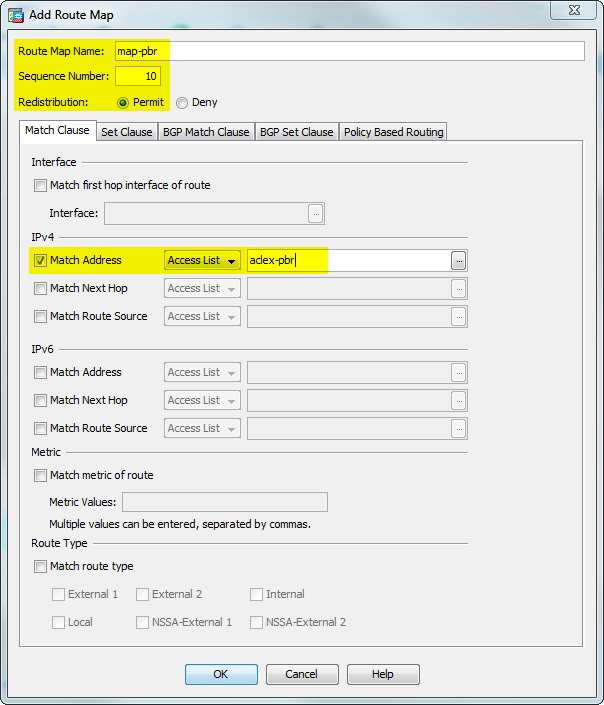
ASA-SJ(config)# access-list pbr-umbrella line 1 extended permit ip 192.168.20.0 255.255.255.0 any4 ASA-SJ(config)# route-map umbrella-pbr permit 10 ASA-SJ(config-route-map)# match ip address pbr-umbrella ASA-SJ(config-route-map)# set ip next-hop 11.11.11.12 ASA-SJ(config)# interface GigabitEthernet1/2 ASA-SJ(config-if)# policy-route route-map.
The Cisco ASA has some interesting characteristics when dealing with traceroute. With most traffic, including ICMP echo, outbound traffic can be inspected to allow the incoming traffic associated with the same flow. Inspecting “ICMP” or even “ICMP Error” does not result in traceroute functioning through the ASA.
The first thing that we need to look at is how traceroute works. Traceroute uses two different types of ICMP packets. Windows systems use an ICMP with incrementing TTL’s to illicit an ICMP TTL exceeded message from each hop along the way. Linux and Cisco use a UDP port with pseudorandom destination port. With the UDP method, an incrementing TTL is still used to illicit a message from each hop along the way. However, the message that is produced at the final destination is often an “ICMP unreachable port-unreachable” message.
Note to reader: All ASA content can be accessed by clicking here (or choosing ASA from the menu at the top of the page).
To understand how traceroute works, it is important to understand the function of the TTL field in the IP packet header. This field is an 8-bit value that works with routers to keep packets from looping forever as a result of network configuration issues. The way this is accomplished is that each router along the way decreases the value by 1. Normal traffic may start out with a TTL of 64, 128, 255 or any other non-zero value. As the traffic traverses a router, this TTL in the IP header is reduced by one.
When a router decreases the value to zero, it drops the packet. When this happens the device will respond with an “ICMP TTL exceeded” if it is in response to an ICMP packet. If a TCP or UDP packet makes it to the final destination without that port listening, the host will respond with an “ICMP Unreachable/Port-Unreachable”. It is worth noting that any device can usually be configured to not respond at all.
Traceroute takes advantage of this behavior and generates a series of packets. The first packet(s) will have a TTL of one and be dropped by the first router. The next packet(s) will have a TTL of two and be dropped by the second router. This is used to build a map of the network. If there is a device configured not to respond traceroute will indicate the presence of a device, but its IP address will not be identified.
With our default ASA configuration, let’s see if traceroute will work.
Windows PC
As we can see, there is no intermediary information. We know that we are not receiving the TTL-exceeded messages from the routers in the network. The ASA requires special configuration to permit the traffic. The first challenge is to permit these TTL-exceeded and port unreachable messages back into the network. This can be done by using an ACL bound to the outside interface.
ASA Config
Now let’s test traceroute again.
Windows PC
Now that looks much better. However, I can see that my ASA is not listed in the path. That is very strange. Upon investigation, I determine that the ASA itself does not decrease the TTL as it passes traffic. Firewalls often play by slightly different rules than a router and this is one of those exceptions. However, we can change this behavior using the set connection option in the modular policy framework (MPF).
ASA Config
Now, let’s test traceroute again.
Windows PC
We can now see an extra hop (75.117.163.238 is an address on my ASA), but there are missing statistics (see the *). This is a result of the fact that the ASA is not responding to all of the traceroute packets. This is due to the rate-limiting of ICMP on the ASA. We can adjust this as well.
ASA Config
Now let’s test this one more time.
Windows PC
Now we can see solid statistics on the first hop. Now our ASA is working correctly with traceroute traffic. I want to show one more example of a way to break traceroute.
Let’s set the IP Audit Attack policy on the outside interface.
ASA Config
Now we can run our test again.
Windows PC

We can see the issue has resurfaced. If we have logging enabled, we can see the IDS engine is detecting this as a “land” attack.
Let’s disable just this one signature.
ASA Config
Now we can retest this once again.
Windows PC
Now you can see that we have a successful traceroute configuration on our ASA. So if I were to receive a lab question that says to make sure traceroute will work through my ASA, that question can mean several things. If I get such a question on the lab and it is vague, I will verify with the proctor exactly what a successful traceroute means. I will also keep in mind that if I enable ids on the ASA that I should probably re-check the traceroute to verify it still works.
Firepower Administrators should also check out – Traceroute through Firepower Threat Defense.
The route maps are like the duct tape for a network. It is not important because it can be used to mend or fix something broken, however, it can be applied to the numerous situation to overtake many issues. It is not the prettiest solutions, but it will be very effective. This route maps are like the 'Then ... IF...' statements of various programming languages. 'If' the specific condition is true and 'then' will do something. The route maps enable to define routing policy which will considered before the router will examine the forwarding table and therefore it can define the routing policy which takes the precedence over the various route processes. Let us see the concepts of the route maps and how powerful it is.
Route maps:
One of the main purpose of the route map in the Cisco router is the customize traffic management beyond the routing tables boundaries. The route maps are mostly used when distributing the routes into the RIP, EIGRP or OSPF routing process. It is also used while generating the default route into the OSPF routing process. The route map also defines which of the routes from a specified routing protocol that are allowed to be redistributed into a target routing process. The route maps have so many features with widely known ACL. The common traits for both are as follows:
They are generic mechanism. The match interpretation and criteria matches are dictated by applying it. Then the same route maps applied to the various tasks may be interpreted differently.
They are the ordered sequence of the individual statements, everyone has the deny or permit result. The evaluation of the route or ACL comprises of the list scan, in the predetermined order as well as an evaluation of a criteria of each matching statement. The list scan will abort when the first statement match is available and the action associated with a statement match is performed.
There are few differences between the ACL and route maps are as follows:
The route maps are very flexible than the ACL and it can verify the routes based on the criteria that ACL will not verify.
The result from an evaluation process of the access list is the no or yes answer. The ACL will either deny or permit the input data. When applied to redistribution, the ACL determines if the specific route can or cannot be redistributed. The typical route map is not only permitted the redistributed route and also modify the information which are associated with the route, when they are redistributed into the other protocol.
Each ACL will end with the implicit deny statements, by means of design convention and there is no same convention for the route maps. If the route map end is reached when matching attempts, then the results depend upon the certain route map application. Since, the route maps which are applied to the redistribution will behave the similar way like ACL and if the path does not match any of the clauses in the route map, then route redistribution is denied, if a route map contained the deny statement at an end.
The route map frequently uses the ACL as the matching criteria.
Given below is the route map logic:
In the nutshell, the route maps will work in the below manner:
This process is whether it is the redistribution process, some other process or policy routing such as NAT- network address translation will call the route map by the text based name. Then the route maps, in turns have the match statements or conditions, that are usually, but it is not always, the extended list or access list. The BGP may match on ASN- autonomous system number or any different attributes. In case, the route maps function during the redistribution as follows:
The below one demonstrates how the route map is applied during the redistribution:
The route map is mainly used to control as well as tag the route from EIGRP when it is redistributed into the OSPF. While processing the OSPF redistribution, the route map titles as set_tag is called there. A route map comprises of 3 parts. The 1st part calls the ACL- access control list 10, that will permit the 172.16.32x network and set the tag of 10. Then the 2nd part calls the ACL 11, that in turns matches the 172.16.1.x IP address. If the match occurs, then the metric can be set in such a way that the route is redistributed. Then it turns into the OSPF type route 1 and finally the tag has to be set to 11. Then the final or 3 rd part of a route map cannot call the ACL, hence all the routes are matched as well as the condition of the set will be applied. In this case, the routers are setting the tag in 300 and you can set the tag to help the network document or else use the tags to find routes which you like to perform or filter some other action.
The route maps have some common characteristics such as;
- The route maps are executed from the lowest sequence of number to the highest sequence. You can modify or edit the maps with the help of sequence number.
- You can use the route maps to deny or permit the information is true by match statements.
- If the match is found in the route map instance, the execution of the other further route map will stop.
- If the route map is applied in the policy routing environments, the packets which don't meet a match criteria are forwarded based on a routing table.
- If the multiple match statements within the single instance of route map is called, then all the match statements should match for a route map instances to obtain the true result.
- As with the ACL, an implicit denies are included at the route map policy end.
- If it is not a corresponding ACL to match statements in an instance of the route map, then the entire routes are matched. Then set statement, in result, apples to whole routes.
- In case, there is no match statement in the instance of the route map, the whole packets and routes are matched. Then the set statement can apply to all the packets or routes.
- You can use the route maps to create the policies based on the packet size, IP address, application, end system ID and protocol.
Route map configuration:
A route map syntax is comprised of roughly 3 separate Cisco commands based on the accomplishing route map and type of process which calling it. When configuring the route map, follow the 5 step configuration process. Based on the application of the route map, additional configuration can also be needed, including with PBR or BGP communities.
Step 1:
Configure any AS_Path, ACL or any match criteria which the route map can be used in a match command. It should be the first, so that you will not call an empty AS_PATH list or ACL.
Step 2:
Configure a route map instance. It is established with a command of route-map name permit|deny sequence number. Assure to leave the room between the sequence numbers for the future modifications or updates. A route map instance along with a lower sequence numbers are executed first.
Step 3:
This step defines a match criteria as well as configure the statements of match which can be used in the single instance of the route map. In case, the absence of the match commands, the entire routes or packets are matched here.
Step 4:
It is the optional step. It defines a set criteria as well as configures set statements which are used in the single instance of the route map. You can also do with a route map configuration set command.
Step 5:
Again, it is the optional step. Configure any AS_PATH, ACL or any match criteria which a route map can use the match command.
Step 6:
Asa Route Map California
Apply a route map, based on the application of the route map, it may be applied in so many ways. Some more common application, such as route redistribution, BGP and PBR.
In the above configuration, 3 primary commands are used to configure the route maps such as a route map command, set commands and match commands.
Asa Route Map Directions
Route map commands:
Here the complete route map syntax is:
Here, the route_map_name is also called as the map tag. It is the text-based route map name. In that the name is logically grouped and unique as well as defined all the route map policies. It is the name which is used to call a route map during the process and redistribution. The deny and permit keywords are always optional and a default keyword is permit. If a route map is called from the redistribution process, then the keywords are set to permit and a match criteria are met for a route map, a route is redistributed. If a keyword is set to deny, in same criteria, then a route might be denied. Suppose a route map is called from the policy routing statement, then match criteria is met for route map as well as a keywords are set to permit, then the packets might be policy routed. If a deny keyword is used, hen the packets are forwarded based on the normal route processes.
The sequence number implies in which order that the statement of the route map has to be executed. While the route maps are called, then a route map with a lower sequence number will execute first. Suppose, the match is not available in a route map with a lower sequence number, a route map with a next higher sequence numbers are executed. Again, this process will repeat automatically until the match is identified or no more route map statement exists. If the match is caught, then the execution for the individual route or packet stops and a next route or packet starts the process with a route map statements with a lower sequence number. There, the default sequence number is 10.
In short, it is the process called the route map by the text based name.
Match commands:
A route map has specific match statements or conditions. It is usually an extended access list or access list. This command also enables you to define the route map criteria. You can also match commands to call the ACL to compare the routes. The match statement can also match the route type, packet length or route tag. In the IP networks, the command enables to match the routes which have the network address matching 1 or more in the prefix list or specific ACL. Use the standard, expanded or extended range ACL. Then the next hop keyword will enable to match the routes which has the next hop addresses matching 1 or more in an ACL. It is most primarily used in the BGP.
Set commands:
Here, the match statements are followed by the set statements. Suppose, the match statement turns the true result or output, then the set statements are executed. These set commands are mostly executed after the successful match being made in a route map instance. This set command may be omitted in some cases, because it is only optional command. The set commands are divided into 2 categories such as routing protocols, or redistribution - certain set commands, policy routing certain set commands, and BGP- certain set commands. If the route maps are used on the redistribution, or simply to filter the networks, it is not necessary to use the set command until you like to tag or influence the route further.
Cisco Asa Route-map Nat
Asa Route Map New York
Asa Route Map Location
The route map is the one which helps in defining the routing policy which will be considered before a router examines the forwarding table. However, it is considered as the perfect solution for the problem, it offers the effective solution which can be applied to different situations to solve the various problems. The configuration of the route maps and its valuable 3 commands are explained in detail. The concepts and characteristic of the route maps give you the idea about the route maps.
Asa Route Map Definition
